Creating an embedded system that can be verified and trusted will lead to more successful deployment in critical industries such as transportation, industrial automation and smart grids. With the combination of embedded Trusted Platform Module (TPM) 2.0 and a comprehensive set of design principles, you can create a robust and highly secure embedded system.
TPM 2.0: Strengthening Embedded Security
A Trusted Platform Module (TPM) 2.0 is a hardware chip designed to enhance and increase security through encryption keys on an embedded rugged and industrial Linux single board computer (SBC). A TPM 2.0 chip is now optional on Venice and Malibu single board computers from Gateworks. The TPM chip used is a Microchip ATTPM20P-H6MA1-10 TPM connected to the SPI bus. This is a TPM 2.0 r116 Trusted Computer Group (TCG) compliant chip.
This TPM chip offers Cryptographic support for:
– HMAC
– AES-128
– SHA-1
– SHA-256
– ECC BN_P256, ECCNIST_P256
– RSA 1024-2048 bit keys
Utilizing TPM for Robust Security Measures
A TPM has become a standard item on modern computing equipment to provide secure systems that can ward off security threats. Having a TPM chip is important because it allows the storage of a security key that is isolated from the main disk and operating system, making it more difficult for threats to gain access.
TPM 2.0 empowers embedded Gateworks SBCs with a myriad of security measures, including:
- Secure Boot Process: Only authorized firmware and software can be loaded, ensuring the integrity of the boot sequence.
- Disk Encryption: Linux Unified Key Setup (LUKS) encrypts storage disks, tethering the decryption process to the system’s Platform Configuration Registers (PCRs), thereby ensuring system sanity.
- Trusted Execution Environment (TEE): Establishes a secure enclave where critical operations can transpire shielded from external interference, bolstering system integrity.
- Remote Attestation: Validates the system’s integrity remotely, thwarting attempts at unauthorized system access.
- SSH Key Protection: Aligns SSH keys with TPM PCRs, fortifying communication channels against potential breaches.
- Hardware-Based Cryptography: Quickly perform encryption and decryption for tools like SSH
TPM & PCRs: Verifying System Integrity
Platform Configuration Registers (PCRs) are registers that represent ‘fingerprints’ of different pieces of a specific system. These pieces can be things such as the bootloader, Linux kernel, and Initramfs. If the stored PCR values in the TPM do not match the currently booting system PCRs, access will not be granted. For example, someone trying to boot a Ubuntu Live CD would not be able to access the TPM key as the PCRs generated from the original disk and stored in the TPM will not match the newly generated PCRs from the boot CD. PCRs use hashing and thus any new value is concatenated with the old and then hashed. This new hash will replace the old hash. The definition of each specific PCR register can be found online.
Using the TPM and Disk Encryption
Encrypting a storage disk is important so that all the data on the disk cannot be read by a bad actor unless it was properly decrypted. Linux Unified Key Setup (LUKS) is the commonly used disk encryption system in Linux. The LUKS header can be tied to the PCRs of the system, forcing everything in the system to be sane and in a trustworthy state before decryption.
Using TPM for Secure Booting
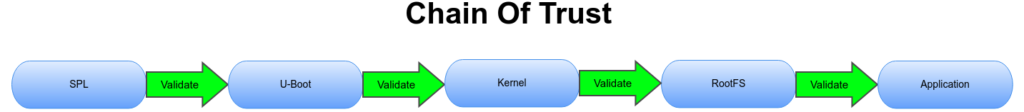
A TPM can help prevent a Linux system from fully booting if something has gone awry. When booting, the system will validate the PCRs and only boot if everything matches. If a hacker has altered any of the boot code, the PCRs will not match and the boot will fail, preventing access. The integrity of the entire system is always checked to be sure nothing has been tampered with. A Linux Root of Trust (RoT) and Chain of Trust can be reinforced with the TPM through the PCRs & secure keys.
TPMs Protect Malicious Malware and Rogue Applications from Sensitive Data
In Linux, a Trusted Execution Environment (TEE) can be set up to create a secure environment on the system where critical operations can take place with enhanced protection. Only authorized software and binaries can be run within the TEE. If some malicious code makes it onto the system, this code cannot interact with or access data in the TEE. This isolation is just another layer of security that can be used. The TPM can be used to verify the system through PCRs before allowing the TEE to be set up and run. Read more about TEE on the Venice family of SBCs.
TPM and SSH Keys
Secure Shell (SSH) is a commonly used communication protocol in Linux. To be secure, keys are used to authenticate the connection. These keys can be sealed to the PCR values in the TPM. If the system has been compromised at all, the key would not match and then SSH would not be allowed to execute or communicate.
Secure Firmware Updates with TPM
Firmware updates can be a security hole to a system if a malicious update is used. An update should only be passed to a known secure system, in which the TPM can provide remote attestation, validating the integrity of the system. In addition, the firmware can be encrypted at the source and then decrypted and authenticated with the keys from the TPM upon arrival on the system. This will prevent malicious firmware from being executed if it doesn’t have matching keys.
Generate True Random Numbers with a TPM

Random numbers can be useful for applications that need obscurity. The TPM has a Hardware Random Number Generator (RNG) that is configured as a FIPS-140-2 compliant Deterministic Random Bit Generator (DRBG). These random numbers will be more robust and secure than those generated by software. The entropy can be used for cryptographic keys, any initialization vectors and other security-related items.
How to Access the TPM on Gateworks SBCs
Linux has a TPM tool set that offers over 100 different commands related to the TPM. They can be installed easily with Linux apt.
apt install tpm2-tools tpm2-abrmd
The TPM is located in Linux at /dev/tpm0 but the TPM Linux commands will default to using this.
More information on specific commands are included on the Gateworks TPM 2.0 Wiki Page.
Conclusion & Security Resources
The TPM hardware chip on the Gateworks SBCs strongly increases the security of the embedded system. The TPM provides a hardware-based root of trust and various other cryptographic functions. The critical PCRs stored and validated by the TPM maintain a level of security to confirm that the system software has not been tampered with or compromised. This provides proof of integrity to the trusted execution environment as well as remote attestation, which is highly beneficial in any remote and distributed environment. Storing and acting as a secure remote hardware repository of cryptographic keys provides a stronger defense when compared to software and disk-based keys. Creating an embedded system that can be verified and trusted will lead to more successful deployment in critical industries such as transportation, industrial automation and smart grids. Using a TPM along with other security practices can create a robust and highly secure embedded system.
- Gateworks Security Considerations for Embedded Designs
- Gateworks Venice Encryption Wiki Page
- Gateworks Linux Encryption Wiki Page
Please note that Security Reference Manuals from NXP are obtained through the manufacturer directly after signing an NDA.
About Gateworks
Gateworks Corporation has been designing and manufacturing high-quality ARM-based single board computers for secure embedded and industrial applications for decades. Our rugged SBC’s are the computing platform of choice for companies who value reliability, long-life availability, and superior technical support. All SBCs are made in the USA and feature industrial temperature parts. Several industrial SBC families have varying sizes from 35x70mm up to 140x100mm with Mini-PCIe slots for expansion. The SBCs feature multiple ethernet (including dual Gigabit) ports as well as multiple Mini-PCIe and M.2 slots for WiFi and Cellular radios. Each single board computer is designed with an optimized and highly efficient power supply that accepts 10-60VDC. To further view the entire line of Gateworks SBCs, please visit the Gateworks Industrial Single Board Computer product page.