Why is security important for embedded communications design?
Security is of the utmost importance for embedded systems that are deployed in any highly critical and important applications. These range from controlling an entire power grid to providing network connectivity in medical, transportation and defense sectors. If anyone with ill intentions gains access and control of an embedded system, the security breach could cause damage to the system, result in loss of finances and exposure of private data, or cause lost productivity. No company wants to face these implications of a security breach. Thus, it is very important to build a robust and secure embedded system. There are many degrees of security and each adds a level of effort to deploy. Below are some considerations about different security tactics and implementations.
Physical Security

The first and foremost important thing is to protect the system from physical access. Security measures may even already be in place in the building or facility where the system resides, making it even more difficult to reach the device. Despite many attacks coming over the network, they can also come through physical access to the device. Before gaining a connection to the device, the attacker must acquire the device and gain access. Simple techniques, such as using tamper proof mounts and mounting in hard to reach locations (hidden or high) can be valuable. Using non-common tamper proof screws may even further inhibit access to an enclosure. The Gateworks SBCs have a tamper feature built into the Gateworks System Controller (GSC). This tamper feature provides a switching circuit that can be connected and used to detect an enclosure being opened. When an enclosure is opened, the circuit will erase a secure key stored in the EEPROM, set a status bit, and produce an interrupt. This extra layer can further protect a system when physical access is attempted. Read more here.
Secure JTAG

The JTAG chain is at the root and core of the entire system. The JTAG chain can hold the processor in reset and allow programming of the onboard flash. If an intruder gains access to the JTAG chain they can compromise or take over the entire system. Gateworks has implemented a secure JTAG access on the Venice family of single board computers. A secure 56 bit key is programmed into the fuses on the processor. This key is used for locking and unlocking the JTAG chain.
Secure Boot / Trusted Boot
While the JTAG security mentioned above is important, intruders could still access the SBC through other channels such as the network. This is why it is important to continue implementing security even at the boot level, often referred to as secure boot.
Various keys exist in the system and are used throughout the boot process. The root key which starts the chain of trust is programmed into the SoC via one-time programmable fuse during manufacturing or firmware deployment. There are many options regarding keys, including symmetric keys which crypt/decrypt is the same key, or asymmetric keys where crypt/decrypt keys are different. The key ‘should’ be stored encrypted in the filesystem or in secure storage, such as a Trusted Platform Module (TPM). A TPM is an optional chip on Gateworks Venice and Malibu SBCs.
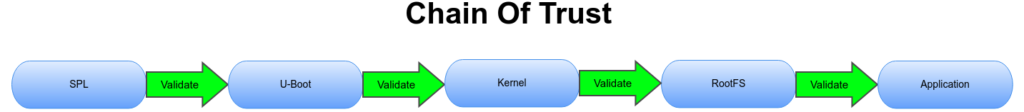
The secure key(s) are read during multiple phases of the booting process. Only if each phase is secure will the rest of the system boot. A chain of trust ensures a that each step of the boot process (BDK, bootloader, kernel, rootfs) is started by the previous step. Each step is secured by a key or mechanism from the prior phase leading up to the final application. To secure the final application, Trusted Execution Environment, or TEE can be used. TEE is where code executed and the data accessed is isolated and protected in terms of confidentiality (nobody has access to the data) and integrity (nobody can change the code and its behavior). Read more about TEE on the Venice family of SBCs.
The i.MX family of processors provides a High Assurance Boot (HAB) feature in the on-chip BOOT ROM responsible for loading the initial program image from the boot media. HAB enables the BOOT ROM to authenticate and/or decrypt the program image by using crypto operations. The HABv4 secure boot feature uses digital signatures to prevent unauthorized code execution during the device boot sequence. This authentication is based on public key cryptography using RSA where the firmware image data is signed offline using a private key and the resulting signed image data is verified on the processor using the corresponding public key hash value programmed into the SoC fuses for establishing the root of trust. SBCs using U-Boot SPL and U-Boot proper for boot firmware support using HABv4 authentication. The i.MX HABv4 also provides an extra optional security operation by using cryptography (AES-CCM) to obscure the boot image so it can not be seen or used by unauthorized users. The Data Encryption Key (DEK) is an AES key used to encrypt and decrypt the boot image.
The Gateworks Newport family of SBCs have an on-chip BOOT ROM that is responsible for loading the initial program image and verifying its signature with optional encryption. There isn’t a HAB component that can be leveraged by other phases but it does support the notion of secure boot. A special variant of the processor is required for Newport SBCs using trusted boot.
Many SBCs also feature ATF (ARM Trusted Firmware). This firmware will ensure the proper kernel and operating system is loaded. Different privelege levels can be set to allow calls into the ATF to request specific items.
Linux Security
Full Disk Encryption
Securing the Linux operating system and programs provides one of the final layers of security. Linux full disk encryption can be provided by the dm-crypt kernel driver/module. File, or file-system based encryption can be provided by the fscrypt or eCryptFS projects. All of these solutions require a key used to encrypt and decrypt. The kernel itself can’t mount a root filesystem that uses encryption so initrd’s (initial ramdisk) are used. This means a ramdisk filesystem is built into the kernel with enough support to mount the encrypted device/file/filesystem.
Application Security
Once Linux is fully booted, the next layer is running application software. A Trusted Execution Environment (TEE) provides a safe environment within the processor for developing and executing secure trusted applications. With TEE, a rogue application installed by attackers could not be ran due to the fact it isn’t a trusted application.
Network Security

A large majority of embedded systems are connected to either a LAN or WAN network. When transferring data, it should be encrypted properly using TLS (Transport Layer Security) / SSL (Secure Sockets Layer). In addition, standard network security such as a firewall should be used. All unused ports should be closed. Strong passwords should be used for network interfaces such as SSH.
Security-First Operating Systems – Ubuntu Core
There are specific Linux distributions that take a security first approach, putting security above everything else. These distributions may be more difficult to work with, but ultimately provide a very secure platform. One such example is Ubuntu Core. Ubuntu core is made specifically for Internet of Things (IoT) deployments. Because Ubuntu Core is designed for devices on the edge, security became a top priority. It uses a stripped down root filesystem and kernel, only using what is essential. Applications and device drivers are packaged and installed as snaps (packages). Applications run in tightly controlled sandboxes, limiting their access to the filesystem, system calls and network interfaces. Security policies can be specifically defined throughout the system to provide top level protection. Security updates are also easily deployed, making it easy to close newly found exploits. Secure boot is used to ensure only authorized software installations. Full disk encryption is used to protect data. With an entire OS built with security in mind, Ubuntu Core may be an excellent choice for highly sensitive installations. Ubuntu Core can be installed on Gateworks SBCs, but typically at a cost through Ubuntu. Visit Ubuntu Core.
CAAM (Cryptographic Accelerator and Assurance Module)
The NXP i.MX6 and i.MX8 SoCs use a CAAM (Cryptographic Accelerator and Assurance Module). The CAAM is an amazing hardware acceleration block used for offloading the heavy encrypting and decrypting functions of a secure system. The i.MX SoC’s have a Hardware Unique Key (HUK) per chip that can be accessed only by the i.MX CAAM. This HUK can be used to encrypt a key and store it in the filesystem during manufacturing. During boot, CAAM is used to decrypt the key and restore the plain key that would be used to decrypt the filesystem. Since the key inside CAAM is not accessible the encrypted key is always protected.
The NXP i.MX CAAM offers:
- Widevine ciper text stealing (AES-CBC-CTS mode)
- PlayReady content protection
- Public Key Cryptography (PKHA) with RSA 4096 and Elliptic Curve (ECC) algorithms
- Real-time integrity checker (RTIC)
- DRM support for RSA, AES, 3DES, DES with Side channel attach resistance
- Side channel attack resistance
- True random number generation (RNG)
- Manufacturing protection support
A Trusted Protection Module (TPM) is also available as an optional component for storing secure keys on Venice and Malibu SBCs.
Conclusion & Security Resources
In summary, security is extremely important on embedded systems. Digital crime only continues to increase as technology proliferates into every aspect of the world. Embedded systems can control entire power grids, oil pipelines and water sources. Keeping these resources safe is crucial. There are many ways to secure the system, from secure JTAG to secure boot. Securing the root file system and each application adds yet another layer. There are a multitude of security techniques that can be used depending on the application. Visit the links below to read through all the specific details to create your own implementation of a secure system.
Please note that Security Reference Manuals from NXP & Marvell are obtained through the manufacturer directly after signing an NDA.
About Gateworks
Gateworks Corporation has been designing and manufacturing high-quality ARM-based single board computers for embedded and industrial applications since 1998. Our rugged SBC’s are the computing platform of choice for companies who value reliability, long-life availability, and superior technical support. All SBCs are made in the USA and feature industrial temperature parts. Several industrial SBC families have varying sizes from 35x70mm up to 140x100mm with Mini-PCIe slots for expansion. The SBCs feature multiple ethernet (including dual Gigabit) ports as well as multiple Mini-PCIe slots for WiFi and Cellular radios. Each single board computer is designed with an optimized and highly efficient power supply that accepts 10-60VDC. To further view the entire line of Gateworks SBCs, please visit the Gateworks Industrial Single Board Computer product page.